N4K Pay-as-you-Go
Overview
Nirmata Enterprise for Kyverno (N4K) is an enterprise distribution of Kyverno available via the AWS Marketplace. This add-on provides 0-CVEs, secure defaults, and operational enhancements - deployable directly to your Amazon EKS clusters.
Prerequisites
- Active AWS account and Amazon EKS cluster (v1.23+)
- AWS CLI, kubectl, and eksctl installed and configured
- IAM permissions to create roles and service accounts
Installation via AWS Console
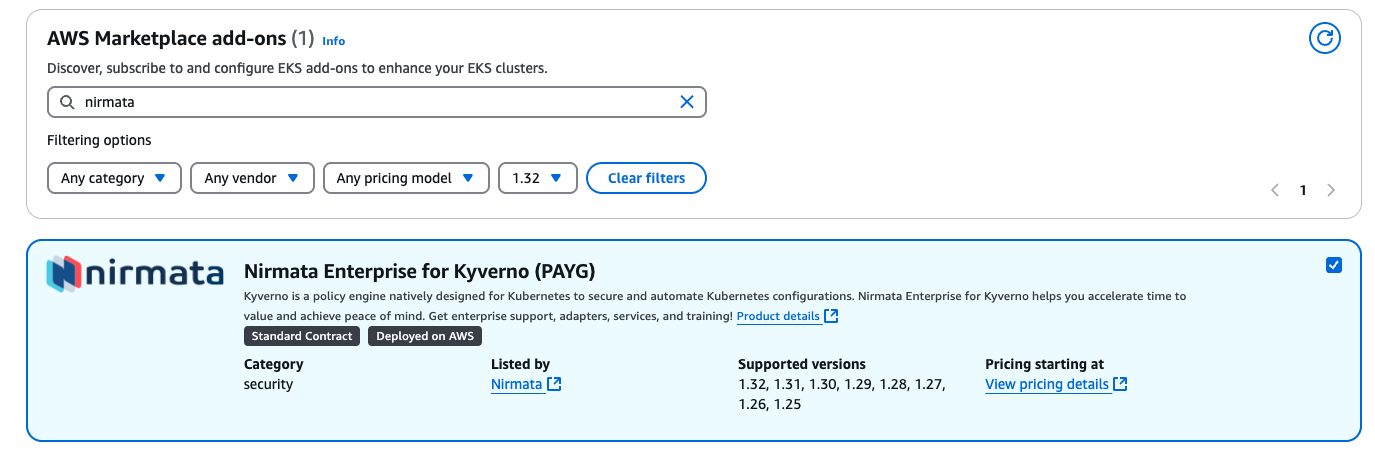
Select N4K Add-on
- Go to Clusters>Add-ons tab and click on
Get more add-ons. - Scroll down to AWS Marketplace add-ons
- In the search bar, type
nirmata - Select
Nirmata Enterprise for Kyverno (PAYG). - Click on Next.
Configure N4K Add-on
- In the
Configurestep, if not already subscribed to N4K from your cloud account, under the Status field, you will see aRequires subscriptionmessage. - Click on
View Subscription optionsand follow the instructions for subscription.
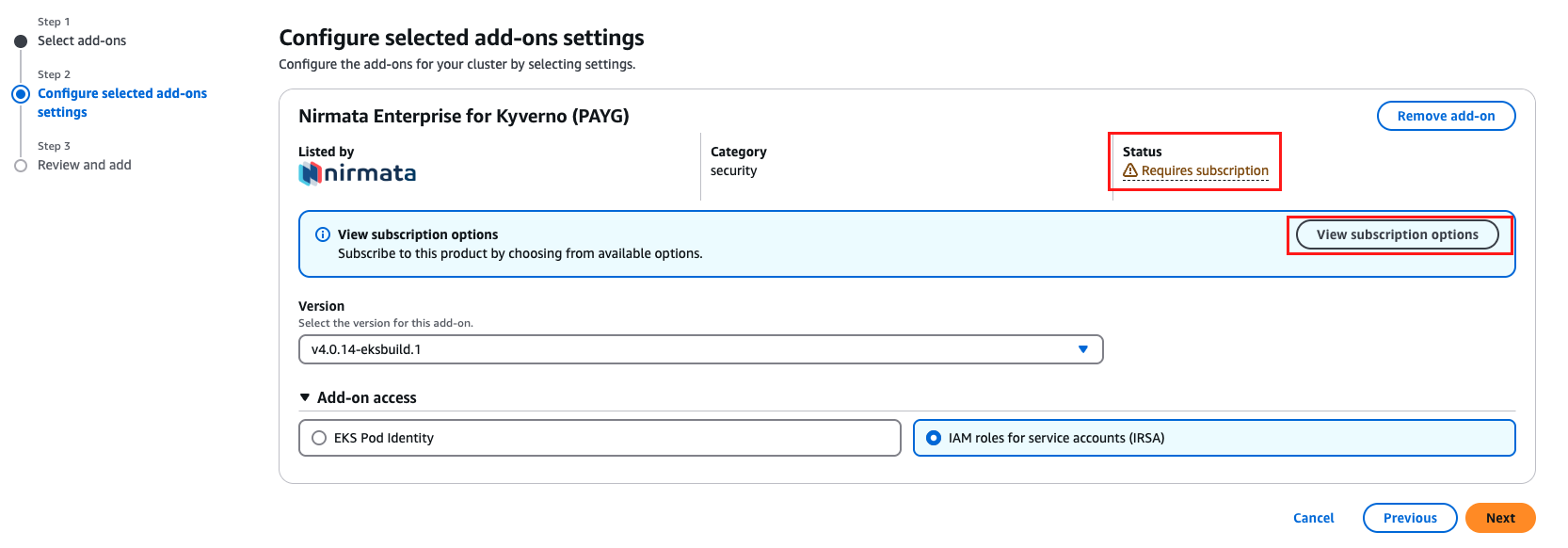
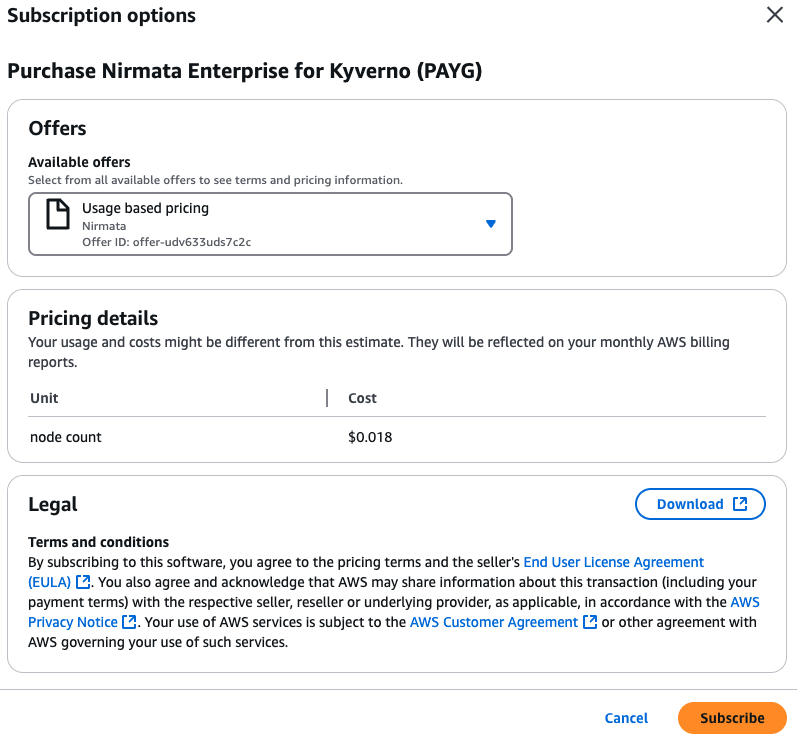
- The add-on requires access to AWS Metering APIs. Select
IAM roles for service accounts (IRSA).
NOTE: You must use the IRSA option and not Pod Identity as there will be issues in hitting the metering APIs resulting in errors in the Kyverno controller pods.
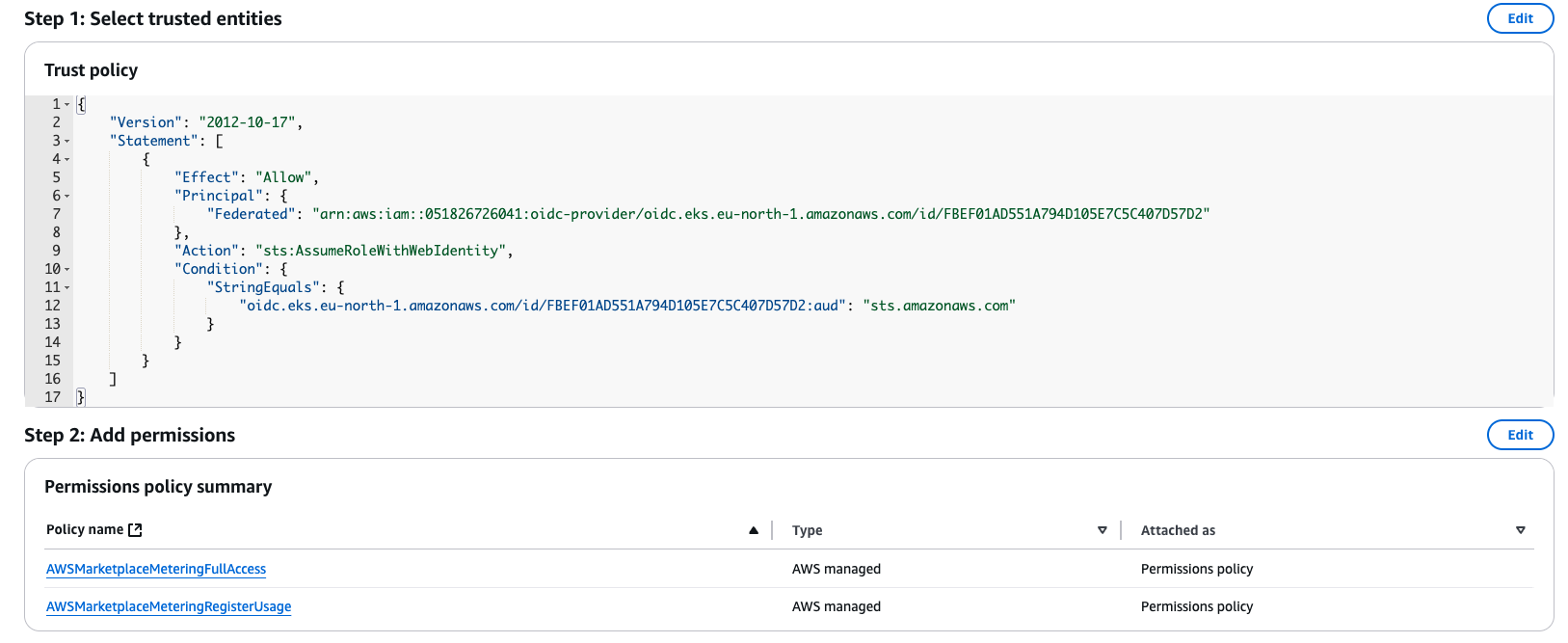
- Create the IAM Role with the following trust relationship policy and permissions.
- Go to IAM>Roles>Create role.
Select Custom trust policy:
NOTE: Refer to the cluster’s OpenID Connect provider URL to add in the trust relationship.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<ACCOUNT_NUMBER>:oidc-provider/<oidc.eks.<REGION>.amazonaws.com/id/XXXX>"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"oidc.eks.<REGION>.amazonaws.com/id/XXXX:aud": "sts.amazonaws.com"
}
}
}
]
}
Add Permissions:
- AWSMarketplaceMeteringFullAccess
- AWSMarketplaceMeteringRegisterUsage
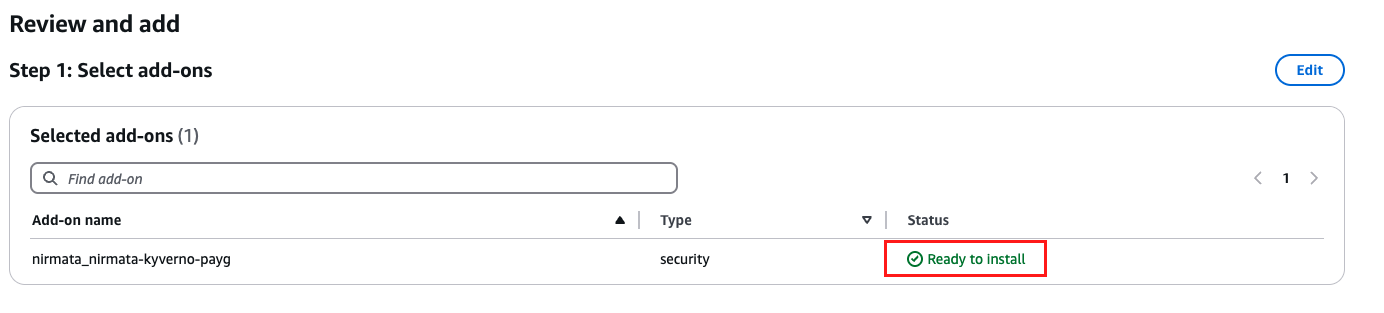
Review and Add
- Review the add-on configuration. The
Statusshould beReady to Install. - Click on Create.
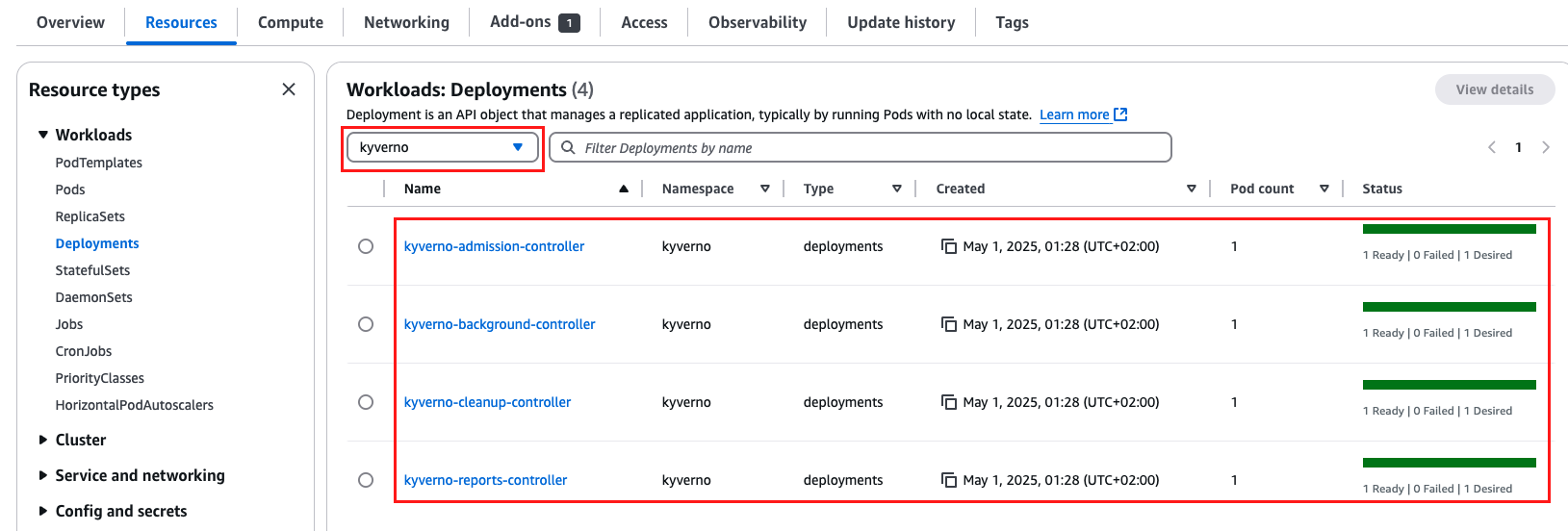
Verify Installation
- Go to Cluster>Resources>Workloads>Deployments.
- Select
kyvernonamespace from the dropdown. - Verify that all four deployments are up and running.
Installation via CLI
Subscribe to N4K in AWS Marketplace
Note: This step needs to be done only once per AWS account.
- Visit the N4K listing.
- Click Continue to Subscribe.
- Accept the terms to enable deployment into EKS.
Set Variables
export CLUSTER_NAME=<your-cluster-name>
export CLUSTER_REGION=<your-cluster-region>
Associate IAM OIDC Provider
eksctl utils associate-iam-oidc-provider \
--cluster $CLUSTER_NAME \
--region $CLUSTER_REGION \
--approve
This step allows Amazon EKS to map IAM roles to Kubernetes service accounts securely.
Create IAM Service Account for Marketplace Metering
To enable AWS Marketplace metering for usage-based billing, N4K requires permissions to report usage. These are provided via the managed policies:
AWSMarketplaceMeteringRegisterUsageAWSMarketplaceMeteringFullAccess
Create the IAM service account:
eksctl create iamserviceaccount \
--name kyverno \
--namespace kyverno \
--cluster $CLUSTER_NAME \
--region $CLUSTER_REGION \
--attach-policy-arn arn:aws:iam::aws:policy/AWSMarketplaceMeteringRegisterUsage \
--attach-policy-arn arn:aws:iam::aws:policy/AWSMarketplaceMeteringFullAccess \
--approve \
--override-existing-serviceaccounts \
--role-only \
--role-name N4K-PayG-Role
This step ensures that N4K can register and report usage data required for AWS billing. No other permissions are required.
Install N4K Add-on in the Cluster
To list available versions:
aws eks describe-addon-versions --addon-name nirmata_nirmata-kyverno-payg --query 'addons[].addonVersions[].addonVersion' --output text
export SERVICE_ACCOUNT_ROLE_ARN=$(aws iam get-role --role-name N4K-PayG-Role --output json | jq -r '.Role.Arn')
aws eks create-addon \
--cluster-name $CLUSTER_NAME \
--region $CLUSTER_REGION \
--addon-name nirmata_nirmata-kyverno-payg \
--addon-version <latest-version> \
--service-account-role-arn $SERVICE_ACCOUNT_ROLE_ARN \
--resolve-conflicts OVERWRITE
Verify Deployment
kubectl get pods -n kyverno
Upgrading the Add-on
To upgrade N4K:
aws eks update-addon \
--cluster-name $CLUSTER_NAME \
--region $CLUSTER_REGION \
--addon-name nirmata_nirmata-kyverno-payg \
--addon-version <new-version>
Uninstalling N4K
To remove the N4K add-on and IAM service account:
aws eks delete-addon \
--cluster-name $CLUSTER_NAME \
--region $CLUSTER_REGION \
--addon-name nirmata_nirmata-kyverno-payg
eksctl delete iamserviceaccount \
--name kyverno \
--namespace kyverno \
--cluster $CLUSTER_NAME \
--region $CLUSTER_REGION
Support
For assistance with setup or usage, contact Nirmata Support.
