Suppress Policy Reports
Kyverno generates policy reports for all namespaces in the cluster. While system namespaces are ignored during admission scans, they are still included in background scan reports. Similarly, third-party namespaces such as those used for monitoring, logging, or internal services (e.g., monitoring, nirmata, etc.) often generate policy violations that cannot be directly actioned by application teams. These reports can introduce noise, making it harder to focus on issues that truly matter.
To help reduce this noise and improve signal clarity, NCH allows users to suppress policy reports from specific namespaces.
What Suppressing a Namespace Does
- Suppressing a namespace hides its policy reports in the NCH UI.
- Reports are still generated by Kyverno and available if needed.
- Suppressed reports are simply filtered out from the default view to allow teams to focus on high-priority workloads and namespaces.
How to Suppress Policy Reports
- Go to Settings>Suppress Policy Reports
- Create one or more Suppression Rules
- Click on Save
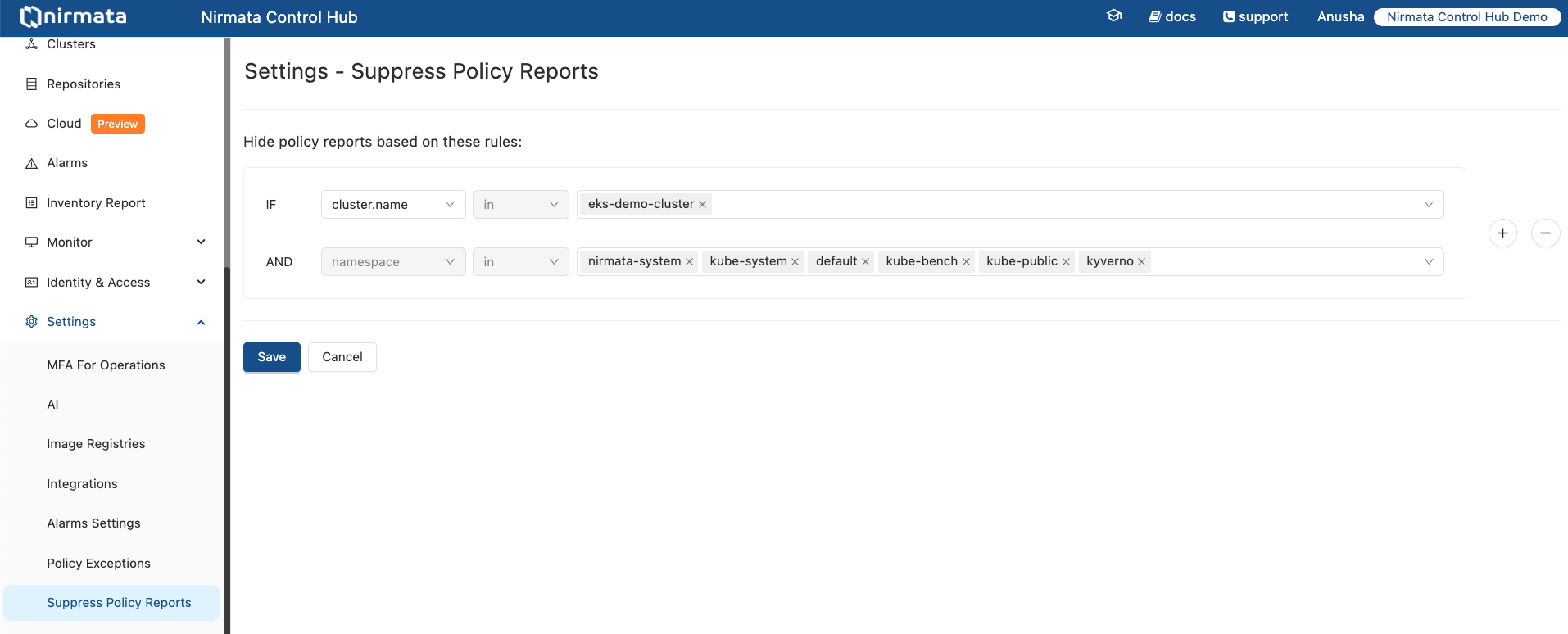
Once saved, policy reports from matching namespaces will be hidden from the default Policy Reports views.
Example Use Cases
- Hide reports from
kube-system,monitoring, ornirmatanamespaces. - Focus attention on application namespaces like
team-a,frontend, ororders.
Notes
- This suppression is NCH-level filtering only. It does not affect Kyverno’s scan behavior or the actual generation of reports.
- All reports remain accessible through the NCH backend and APIs.
